It is estimated 60% of corporate data is held in the cloud, most of which residing in either Microsoft Azure or Amazon Web Service (AWS), which happen to be the top two cloud service providers.
As more businesses switch to hybrid working patterns, increasing workload naturally raises security concerns as well as in-house security teams transferring part or all their infrastructure management to third-party vendors.
Regardless of the chosen platform, organizations expect cloud services to deliver better business agility while ensuring a secure environment for cyber resilience. Both Azure and AWS promise to provide robust solutions to security concerns, as well as cut costs often associated with data centres, offering scalability, flexibility, and improved efficiency within the workplace, among other benefits.
In this article we’ll look at the two tech giants through a cybersecurity lens – discussing different categories of cloud-based security to help you decide which platform best suits your business’s needs. We’ll also discuss how Azure and AWS can integrate as a multi-cloud approach and explore what this involves.
Identity and Access Management
Under the cloud security umbrella lies Identity and Access Management (IAM). With an IAM framework in place, IT managers can control user access to critical information within their organizations. Azure and AWS offer a slightly different approach:
Azure:
Microsoft’s approach to this is based on Active Directory. If you’re already in the Microsoft sphere, using services such as Azure, Power Platform, Dynamics 365 and Intune, you automatically gain access to basic Azure AD features within your subscription. The tier included offers cloud authentication, unlimited single sign-on (SSO), multi-factor authentication (MFA), and role-based access control (RBAC).
AWS:
Like Azure, Amazon Web Service IAM is free for AWS customers. As well as tight access controls, the feature offers logical organization, groups, roles, multi-factor authentication, real-time access monitoring and JSON policy configuration.
Virtual Private Network
VPN is a useful tool for accessing a private network for data transfer between a public cloud and the data centre. VPN systems ensure encryption of data across the internet, offering a high-level of security for users. AWS Virtual Private Cloud and Direct Connect are their two services to enable VPN. Azure offers similar, such as ExpressRoute and Virtual Network, with the only difference being that AWS uses layer 2 routing while Azure uses layer 3.
Monitoring
A highly critical tool for data security, monitoring is a method of overseeing and managing the operational workflow in a cloud-based environment. AWS CloudWatch provides monitoring functionality and ensures a smooth integration of services. Azure Monitor has the ability to track all Azure services as well as monitoring running applications via Azure Application Insights.
There is little difference in the quality of features offered by Azure and AWS in monitoring terms, the only distinction is in the organisation of features and that the free tier of AWS Cloudwatch offers more capability than the limited Azure Monitor trial which requires a paid Azure Log Analytics subscription.
Key Management and Encryption
Here we will discuss Amazon S3 and Azure Blob Storage…
Data protection via Amazon S3 is easy to implement when already utilising the AWS cloud. Data can be protected in transit using Secure Socket Layer/Transport Layer Security or client-side encryption. In terms of Azure, Azure Blob Storage offers similar functionality to Amazon S3, offering both server-side and client-side encryption with AES-256 symmetric keys. Both platforms offer managed key storage. AWS does seem to have more encryptions services, but whether the additional functionality is needed will depend on your individual business case.
Data Centre Security
Access to data centres is tightly controlled by advanced security measures at every level, including perimeter fencing, security officers, locked server racks, alarm systems and 24/7 video surveillance and multi-factor access control. Only authorised personnel have access to Microsoft’s data centres. AWS is also highly secure. All AWS employees who need access have to provide valid business justification and apply for access – as well as requests being time limited and only able to access limited areas of the centre – what is absolutely essential.
Multi-cloud security and identity with Azure and Amazon Web Services (AWS)
Organizations are starting to find themselves taking a multi-cloud approach. To put it simply, this is a model that leverages multiple cloud services, so organisations can reap the benefits from each individual service and avoid being locked in with a single service provider. In a multi-cloud environment, however, it’s critical to ensure there’s consistencywhen it comes to security – cyberattackers love finding gaps within your security systems, so it is important to ensure both your providers are communicating with each other and meeting your organisation’s needs.
According to Microsoft, maintaining security and consistency across cloud environments needs to factor in the following:
Multi-cloud identity integration, strong authentication and explicit trust validation, Cloud Platform Security (multi-cloud), Microsoft Defender for Cloud, Privilege Identity Management (Azure) and Consistent end-to-end identity management.
Multi-cloud identity integration:
Multi-cloud customers may benefit from joining identity services between these two clouds such as Azure Active Directory (Azure AD) and Single Sign-on (SSO) services. This allows access to services in both clouds to be consistently accessed and thoroughly governed.
The role-based access controls in Azure AD can be enabled across the Identity & Access Management Services in AWS (using rules to register the user.userprinciplename and user.assignrole attributes from Azure AD into IAM permissions). This method leads to a reduction of unique identities users/administrators need to maintain across both clouds, consolidating the identity per account deployed by AWS. The IAM solution provided by AWS recognises Azure AD as a federation and authentication source for consumers. You can find out more about how the integration works by watching this tutorial.
Strong authentication and explicit trust validation:
Security engineering teams need to ensure they are implementing strong authentication solutions in a hybrid identity model, and disregard legacy authentication methods, mainly linked with on-premises and legacy Microsoft technologies. Multi-factor authentication (MFA) and conditional access (CA) can be combined to boost security in the authentication process. MFA itself already provides an increased level of security as users have to confirm their identity, however additional controls can be applied using CA controls to block legacy authentication in both Azure and AWS infrastructures. The combination of MFA and CA policies results in strong authentication (when using only modern authentication clients).
Cloud platform security:
The Cloud Platform Security (CPS) service of Microsoft Defender for Cloud Apps can be used to discover, monitor, assess and protect these services. Within the Cloud Discovery dashboard, those within the security operations team can review the apps and resources used across AWS and Azure cloud platforms.
Once services are approved for use, these can be managed as enterprise applications within Azure AD to enable SSL for the convenience of users. CPS also enables users to assess the cloud platforms connected for compliance using the individually specific security/configuration controls.
This overview enables organizations to have a single consolidated dashboard of all the cloud platform services along with their compliance status. Access and session control policies are available within CPS to protect your infrastructure from risky endpoints or users when data exfiltration or malicious files enter your IT systems.
Microsoft Defender:
This function provides integrated security management and protection against threats across hybrid and multi-cloud workloads (Azure and AWS). The defender supports the discovery of security vulnerabilities, the ability to block malicious activity, detect threats using data intelligence, and respond quickly during a cyberattack.
Microsoft recommends connecting an account with the Classic cloud connectors experience or the Environment settings page (in preview) to protect your AWS-based resources.
Azure Privileged Identity Management:
To help control access for your accounts in Azure AD, Privileged Identity Management (PIM) can provide just-in-time access (on an as-needed basis) to services for Azure cloud services. This can help to reduce the risk of privileges that attackers can exploit. Microsoft defines its use as ‘Once deployed, PIM can control and limit access using an assignment model for roles, eliminate persistent access for these privileged accounts, and provide additional discover and monitoring of users with these account types.’
Once combined with Microsoft Sentinel, workbooks and playbooks can monitor and raise alerts to your security operations team when accounts have been compromised or under threat.
Reliable, consistent end-to-end identity management:
All processes include an end-to-end view of the multi-cloud system as well as on-premises systems and training is included for security and identity personnel.
Using a single identity across Azure AD, AWS Accounts and on-premise data, enables an end-to-end strategy as well as heightened security and protection of accounts for both privileged and non-privileged users.
To reduce the burden of maintaining multiple identities in their multi-cloud strategy, often utilise the benefits of Azure AD to provide consistent and reliable control, auditing and detection of anomalies and incorrect use of identities within their environment. As new capabilities within the Azure AD ecosystem grow, businesses can stay ahead of threats which occur because of using identities as a common control plane in a multi-cloud infrastructure.
Here, we’ve provided some of the basic benefits of adopting a multi-cloud approach:
Reducing risk – if one of the cloud providers ever has a failure, your performance may decrease until this is fixed. However, with a multi-approach, you can switch into another vendor.
Competitive pricing – Due to the emergence of cloud providers over the past few years, you have the ability to compare prices and select the best offer that suits your organisation, enabling you to make a well-thought-out decision and conduct an agile plan for your cloud environment.
Scalability – Multi-cloud can help organisations to coordinate workloads and arrange data and infrastructure across multiple cloud environments, regardless of how much data you work with.
Robust security – third-party providers are responsible for maintaining the security of their infrastructures, so you can match their capabilities to suit your needs and ensure your environment is kept secure.
It is important to measure the pros and cons of a multi-cloud approach against the priorities of your organisation – it is not a one-size fits all solution, and some organisations prefer to have a single vendor.
So, time for the ultimate question. Which platform wins on security strategy?
Whilst Azure and AWS both have very secure and powerful tools to host architecture, it does come down to your business needs. It is worth noting that whilst AWS dominates the market share, more than 95% of Fortune 500 companies rely on Azure to provide trusted cloud services, AWS customer tend to be either ‘born in the cloud’ organisations such as Netflix and AirBnB or e-retailers.
Microsoft has over 3500 cybersecurity experts working continuously to keep Azure secure and up to date, as well as an extensive threat intelligence operation. AWS numbers are lower, but they don’t have a comparable Office 365 and Microsoft Dynamics ecosystems to secure, they only offer IaaS/PaaS, SaaS is the vendors or customers issue to secure. If your business already utilises the Microsoft suite of services (Teams, M365 etc) this may be the best option for a seamless integration but both offer good general security.
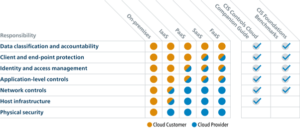
Shared responsibility model
All cloud providers offer a version of their shared responsibility model, which details the respective responsibilities between the customer and the provider for security and data governance, these vary dependent on the type of cloud service you are using; IaaS, PaaS, SaaS or FaaS (Function as a Service). The one below is a vendor neutral one from the Centre for Internet Security which details these:
Book your free Microsoft Azure Assessment today
Fordway’s Microsoft Azure Assessment will provide you with an end-to-end review of your organisation’s Azure subscriptions and associated services.





